Pinger Man is a modern uptime monitoring app we launched earlier this year. It can monitor your application as frequently as 10 seconds and send you downtime notifications via Email, SMS, Twitter, Slack and Web Hooks.
Global Checks
Pinger Man monitors your website from multiple locations across the world. These are used to prevent false reporting of downtime.
Advanced Monitoring
Pinger Man is one of the most feature packed uptime monitoring solution with advanced HTTP monitoring features such as custom HTTP headers, HTTP status code handling and HTTP authentication support.
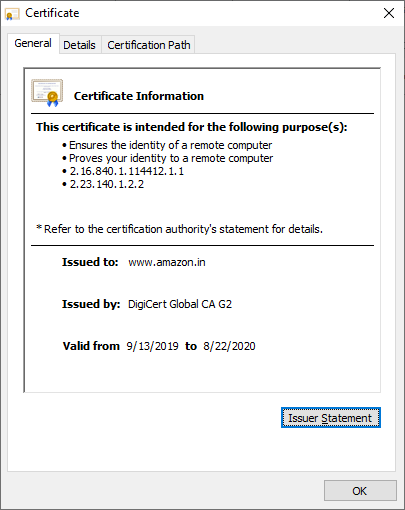
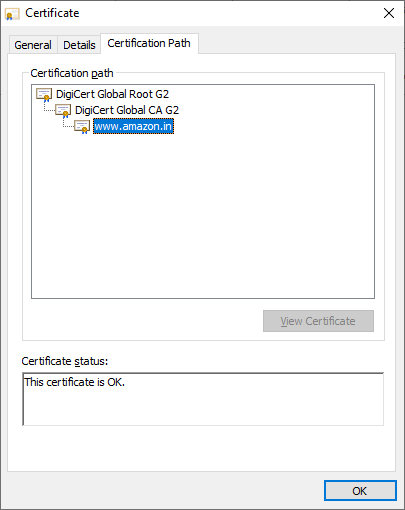
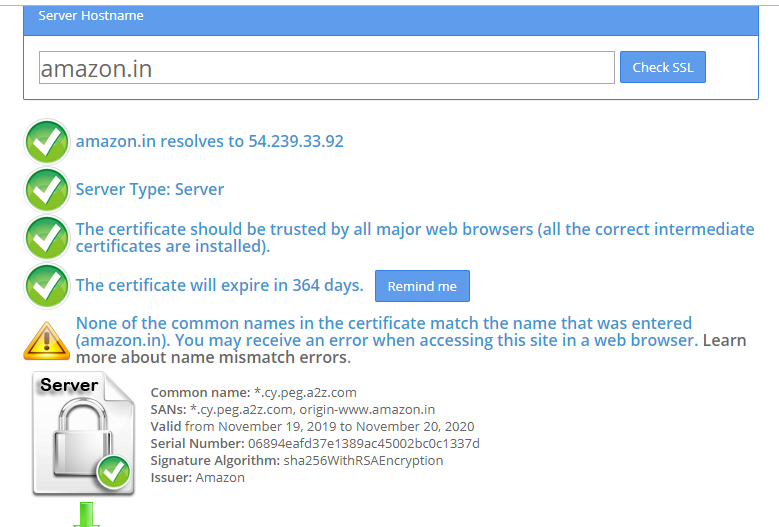
SSL Monitoring
The SSL monitoring feature automatically reminds you to renew your SSL certificates before they expire. It also tracks SSL validation failures.
Public Status Pages
Public status pages can keep your visitors informed about the status of your services. You can even use your own domain to host the status page.
Weekly Reports
Weekly reports give you a summary view about all your monitors right in your inbox.
Maintenance Windows
Scheduled maintenance can be setup to exclude once or recurrent time periods from monitoring.